More consumers are turning to tablets and smartphones to shop, but this back-to-school season major retailers are using mobile to drive traffic to stores, not necessarily to encourage online transactions.
That's not to say that brick-and-mortar retailers don't allow for purchases in mobile apps -- Walmart, the world's largest retailer, has seeded shopping in its mobile app, as have JC Penney, Target and others. Yet mobile commerce doesn't seem to be a major theme for the back-to-school season. Instead, retailers are using mobile marketing to help customers once they're at physical locations rather than to encourage them to buy through mobile devices.
"By and large, the majority of retailers at the moment are using mobile to add to the in-store experience," said Geoffrey Handley, co-founder of Meredith Corp. mobile agency the Hyperfactory.
Consumers are expressing interest in shopping on mobile devices, especially when it comes to tablets. (Though at this point, it's pretty much an
iPad-only game; even Google, whose Android software competes with
Apple's, launched its new Catalog app on iPad first.) The National Retail Federation found that nearly 40% of college shoppers and 30% of K-12 shoppers with tablets say they plan to use them to purchase products for school this year. That's a greater percentage than those who said they would use the device to compare prices or conduct product research, according to the survey of more than 8,000 respondents.
But with smartphones, it's a different picture. Consumers are less enthusiastic about making purchases: Nearly 20% of K-12 shoppers and 17% of college shoppers say they will make purchases with their smartphones. But more than 30% in both camps saying they will compare prices with those devices.
For mobile commerce, online retailers are definitely leading the way. In 2010, eBay reported nearly $2 billion in gross merchandise volume from mobile. The company expects to double that to $4 billion in mobile sales this year.
"The area of [mobile-]commerce is definitely growing, but most retailers are still heavily invested in stores," said Mr. Handley. "Mobile provides a quick win when it aids retail."
Here, Ad Age highlights retailers' mobile apps and strategies for back-to-school and beyond.
TopShop
U.K.-based retailer TopShop has teamed up with SCVNGR, a location-based mobile gaming app, in an effort to get shoppers into its stores this season. Beginning Sept. 5, anyone near a store can play using the SCVNGR app. Players choose the reward they want, such as a 20% in-store discount or a shopping spree, and complete challenges like taking a picture of their favorite back-to-college outfit at TopShop in order to earn points toward the reward.
Finish Line
Earlier this month, Finish Line unveiled a new app that gives shoppers access to real-time inventory at the store nearest them. Users can check to see if an item is available in the style, size and color they're looking for. Transactions can be completed on the app, but it also uses geo-tracking to provide store information and directions from the user's location.
Wet Seal
The teen retailer is taking a different approach to mobile this back-to-school season by offering shoppers a free Android phone (with a new two-year plan plus data) just for coming into a story and trying on jeans. Talk about a traffic driver.
Amazon Student
Launched just in time for the back-to-school shopping season, Amazon's new app allows students to check prices and comparison shop by scanning barcodes. Users can also scan the barcode of an item they no longer want -- think books, games, movies and electronics -- to find out its trade-in value, redeemable for Amazon gift cards.
Google Catalogs
This free app for tablets enables shoppers to browse and interact with catalogs. There are all the expected bells and whistles -- find products in store, buy online, watch related videos -- as well as some cool extras, such as the ability to create collages, search for products across different catalogs and add a retailer to a favorites tab for immediate notification when a new catalog hits. Launch partners include: Anthropologie, Bloomingdale's, Crate and Barrel, L.L. Bean, Macy's, Nordstrom, Sephora, Williams-Sonoma and others.
E-Textbooks
College bookstores beware. A bevy of apps have popped up that allow students to compare prices on new, used, electronic and rental textbooks by scanning a barcode. Students can also rent or buy directly via the app. Chegg, CampusBooks and Kno are a few of the companies playing in the space. And why not? The National Association of College Stores estimates that the average full-time student spends $483 annually on course materials.





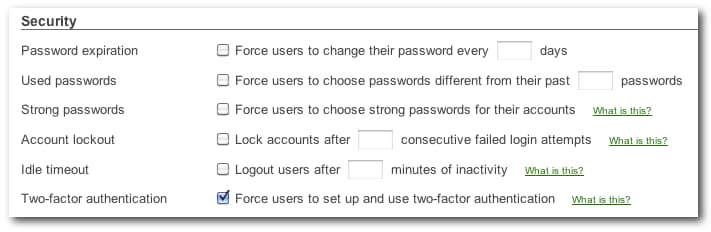
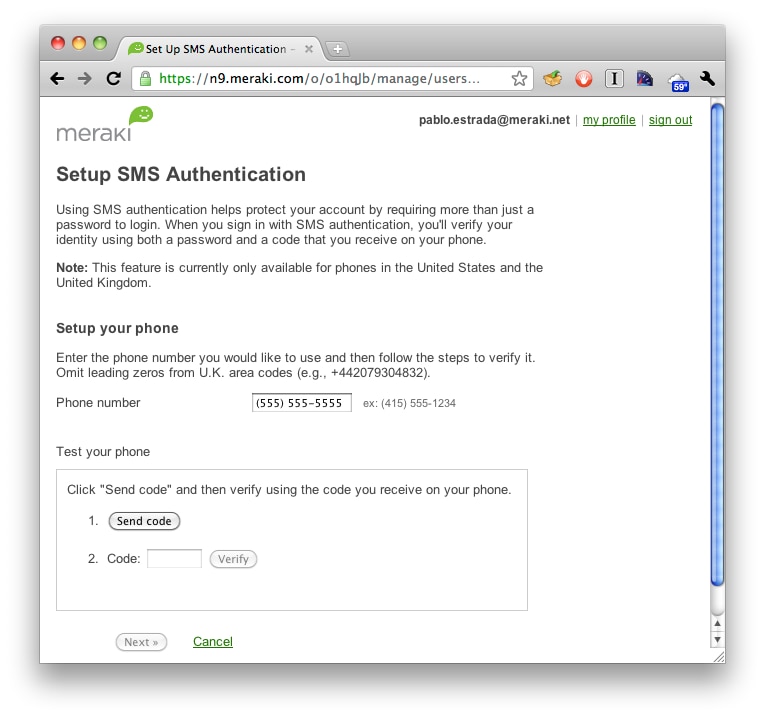
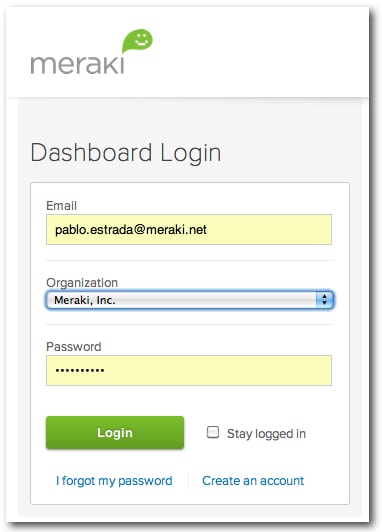
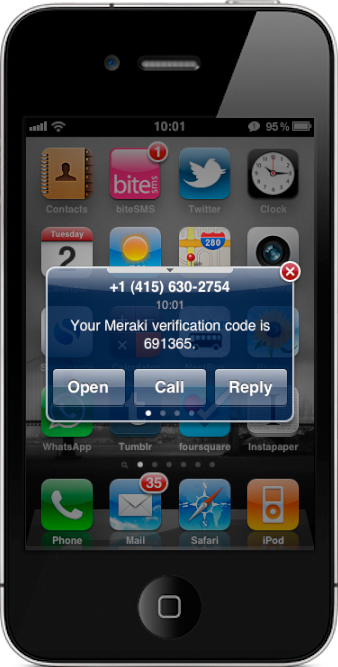
 Security
Security